Opportunistic hackers demand Bitcoin ransom after deleting files from Iomega network drives
Nefarious hackers are wiping files on publicly accessible storage devices and leaving just a Bitcoin ransom note behind.
According to users on the BleepingComputer forums, files on their Lenovo Iomega NAS (network attached storage) devices are allegedly being deleted or hidden. The attackers are demanding Bitcoin in exchange for the safe return of victims’ files.
After the attack, victims are finding their NAS drives empty, except for a text file with the name “YOUR FILES ARE SAFE!!!” One of the ransom notes outlines the attackers’ demand of 0.03 Bitcoin ($280). In this instance, attackers give the victim a deadline of August 1, 2019 to make the payment, or else the files will “be gone for good.”
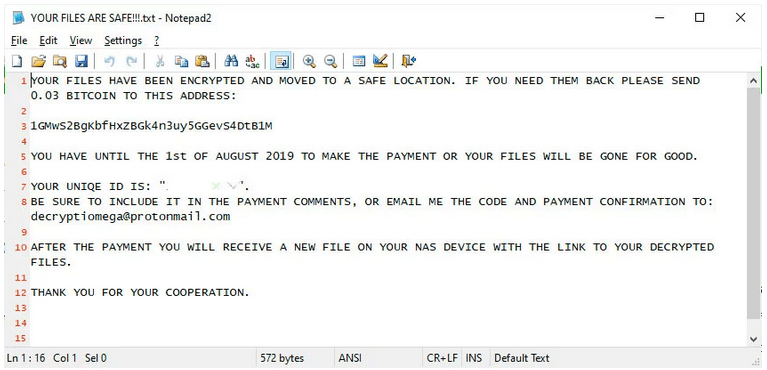
It appears attackers are generating new messages for each victim. That said it’s not immediately clear if it’s the same group of hackers responsible for all the attacks.
Each ransom note appears to list a different Bitcoin address and the amount of Bitcoin hackers demand varies between 0.01 ($100) and 0.05 ($470) Bitcoin.
These are relatively low amounts for data ransom attacks, which have been known to go into six figures. Given that these attacks are most likely on individuals, hackers might be hoping that the low price is enough to lure victims to pay, rather than go through the stress of file recovery themselves.
Sadly, it looks like it might have worked on a few victims.
One of the Bitcoin addresses used in the attack has received nine payments since June 27 which, according to BleepingComputer, could be associated to this campaign. The address has received a total of 0.2 Bitcoin ($1,900).
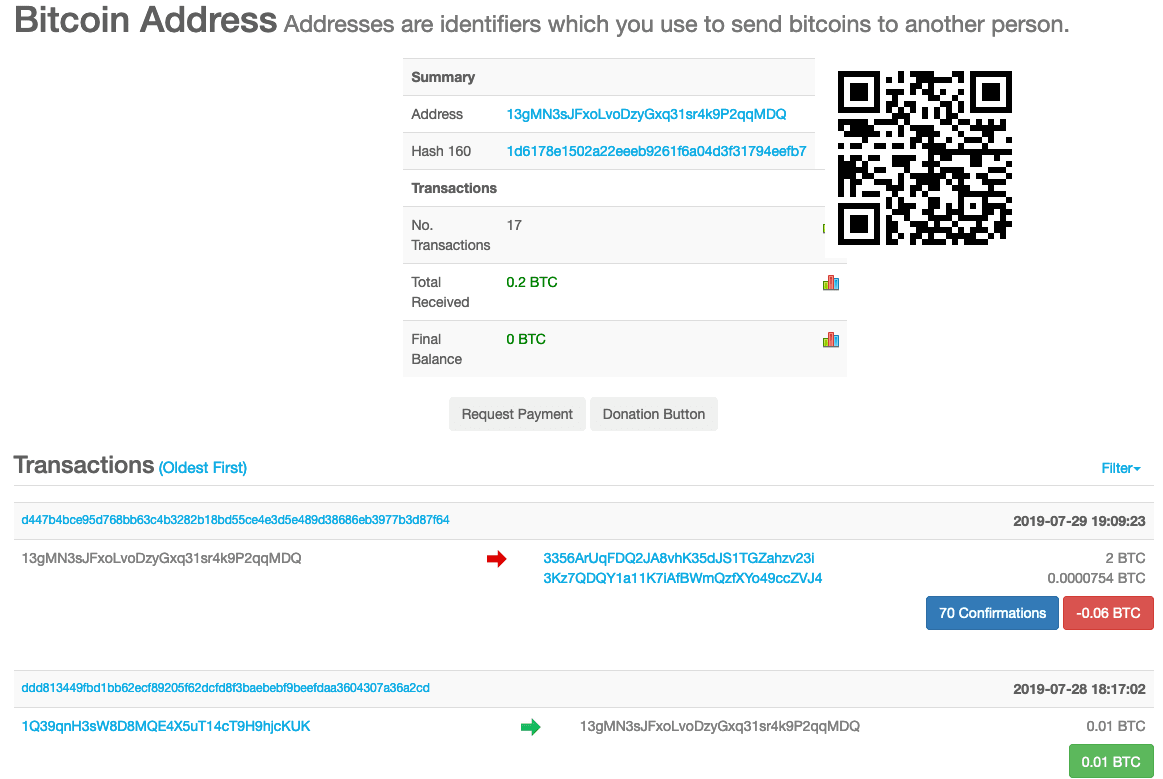
Initial reports confirm that, unlike typical ransomware attacks, files are being deleted rather than encrypted.
One victim said they managed to use file recovery software to recover their lost files, by attaching his NAS drive directly to their PC.
While it’s not been confirmed how hackers are gaining access to these network drives, BleepingComputer found there are numerous unsecured Iomega NAS drives directly attached to the internet. So it sounds like it might be quite straightforward.
Iomega network storage devices have a publicly accessible front-end, so users can access their files over the internet. This is a great feature if you want to run your own “cloud” on your home network, but if you don’t appropriately secure it, the device will be open for the world to see.
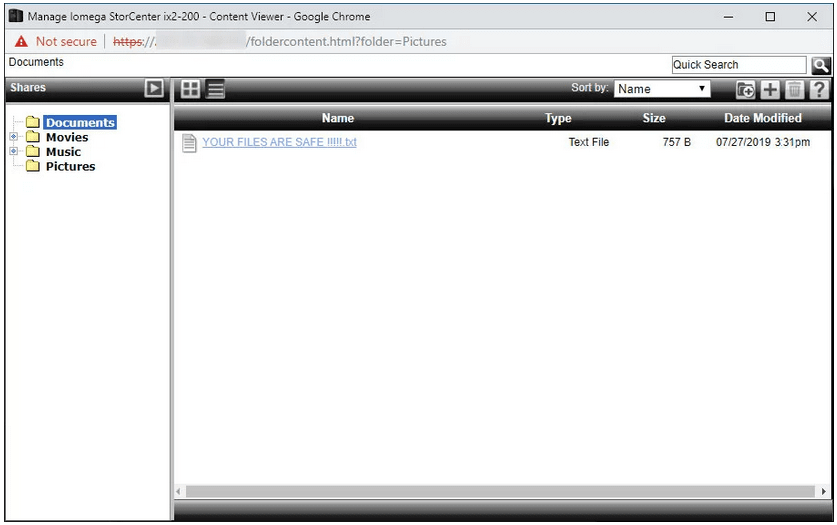
One victim admitted that they hadn’t secured their Iomega NAS drive sufficiently, and suspected this was exploited by hackers in the attack.
Lenovo issued an advisory note last year telling users of its Iomega NAS drives to upgrade the firmware and to properly secure the device.


