Massive DDoS attack on Dyn causes internet disruption, hacked IOT devices blamed
A major cyberattack affected hundreds of websites, including the New York Times, Reddit, Twitter, Spotify, and eBay. The attack was actually centered on Dyn, a New Hampshire-based company that offers a platform to optimize websites’ online performance. This includes monitoring and controlling applications and infrastructure with data and analytics to reroute traffic and ensure end-users aren’t impacted by slow response times.
The massive and sustained Internet attack was launched with the help of hacked “Internet of Things” (IoT) devices, such as CCTV video cameras and digital video recorders, new data suggests.
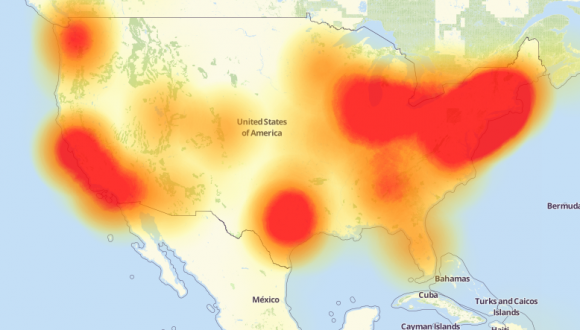
Dyn’s DNS service acts as a bridge between human-readable domain names and IP addresses that the internet is able to understand, and it was customers of this managed DNS service that were impacted. The distributed denial-of-service (DDoS) — an attack where the target is overwhelmed with a deluge of data to cause the network to crash — was felt mainly on the U.S. East Coast from around 11 a.m. UTC (5 a.m. ET), though Dyn reports that service was restored as of 13:20 UTC (07:20 a.m. ET).
DDoS attacks have seen a notable increase in recent times, with reports indicating a rise of 125 percent between 2015 and 2016. Game developer Blizzard has experienced a spate of DDoS attacks in recent months, causing widespread disruption for fans of World of Warcraft, Hearthstone: Heroes of Warcraft, and Overwatch.
Founded in 1998, Dyn claims that “eight of the top 10 internet services / retail companies in the Fortune 500” use its services, and it raised a chunky $50 million round earlier this year, taking its total funding to around $100 million.
DYN gave the following update
Attack Timeline
Starting at approximately 7:00 am ET, Dyn began experiencing a DDoS attack. While it’s not uncommon for Dyn’s Network Operations Center (NOC) team to mitigate DDoS attacks, it quickly became clear that this attack was different (more on that later). Approximately two hours later, the NOC team was able to mitigate the attack and restore service to customers. Unfortunately, during that time, internet users directed to Dyn servers on the East Coast of the US were unable to reach some of our customers’ sites, including some of the marquee brands of the internet. We should note that Dyn did not experience a system-wide outage at any time – for example, users accessing these sites on the West Coast would have been successful.After restoring service, Dyn experienced a second wave of attacks just before noon ET. This second wave was more global in nature (i.e. not limited to our East Coast POPs), but was mitigated in just over an hour; service was restored at approximately 1:00 pm ET. Again, at no time was there a network-wide outage, though some customers would have seen extended latency delays during that time.
News reports of a third attack wave were verified by Dyn based on our information. While there was a third attack attempted, we were able to successfully mitigate it without customer impact.
Dyn’s operations and security teams initiated our mitigation and customer communications process through our incident management system. We practice and prepare for scenarios like this on a regular basis, and we run constantly evolving playbooks and work with mitigation partners to address scenarios like these.



